To integrate OKTA SSO:
Step #1: Register your app in the OKta.
- Log in to OKTA Portal (https://developer.okta.com/login/).
- Menu: choose “Applications” option -> “Create App Integration”.
- Select OIDC – OpenID Connect and Web application as Application type and Click “Next”.
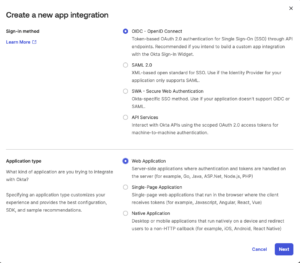
- On the configuration screen you need to set option as in the screen below:
• Grant type – select “Authorization code”.
• Sign-in redirect URI :https://tomhrm.app/oauth/authorize/{your_workspace_name}Important: {workspace} should be value from your tomHRM app.
• Sign-out redirect URIs: https://tomhrm.app/
• At the assignments section select which groups should have access to the SSO or allow everyone in the organization to access.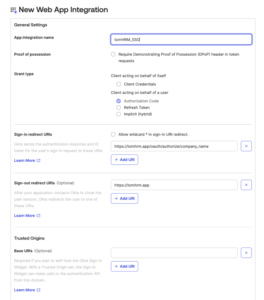
- Copy and save in some safe document Client ID and Client Secret. You will need it later.
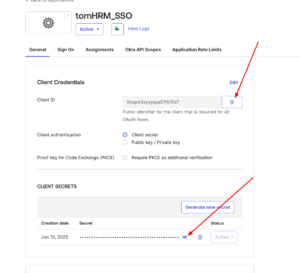
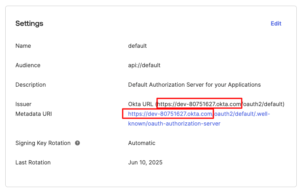
- Visit next from the main menu at OKTA: Security -> API. Click the default OKTA authorization server name (default).
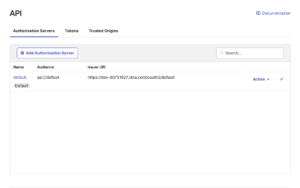
- Find, copy and paste in the safe document the Issuer OKTA URL. You will need that URL in the next steps. (Only the part marked as red below).
- Go to Access Policies tab and make sure that there is at least one policy. If it doesn’t exists then “add rule policy” with the following settings:
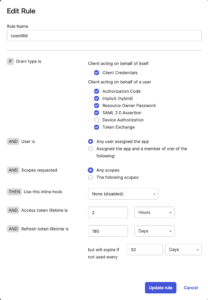
You can adjust settings with the security policy and requirements of your company.
Step #2 – configure OKTA in tomHRM app.
- Visit https://tomhrm.app/login
- Log in to your account as admin and go to Settings > Settings > Authentication. Turn on “Open ID & OAuth 2.0”. Fill the form according to the following guidance:
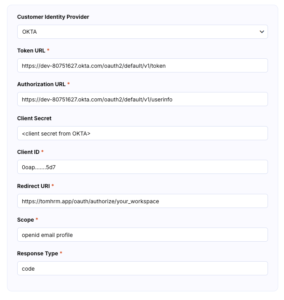
- Choose Identity provider as OKTA.
- Token URL:
You need to create token URL based on your Issuer OKTA URI which you copied at step 7 above. Get that URL and add at the end: oauth2/default/v1/token, so your URL will looks like: https://dev-80751627.okta.com/oauth2/default/v1/token
dev-80751627.okta.com at the above example should be your unique URL from OKTA. - Authorization URL is your OKTA URI and: oauth2/default/v1/userinfo (same pattern as in the point above). So the final URL should be like: https://dev-80751627.okta.com/oauth2/default/v1/userinfo
- Redirect URI: https://tomhrm.app/oauth/authorize/{workspace}
Important: {workspace} should be value from your tomHRM app. - Client Secret – paste saved Client Secret which you copied at step 5 above.
- Client ID – paste saved Client ID which you copied at step 5 above.
- Scope must be: openid email profile
- Response Type must be: code
- Save the form and try to log-in to tomHRM by using SSO login link at the tomhrm.app.
REMEMBER! The tomHRM application recognizes users by their e-mail address or user ID. User emails should be the same in the tomHRM application and in their OKTA account.
