Step 1 – Register app in Azure Active Directory
- Log in to Azure Portal
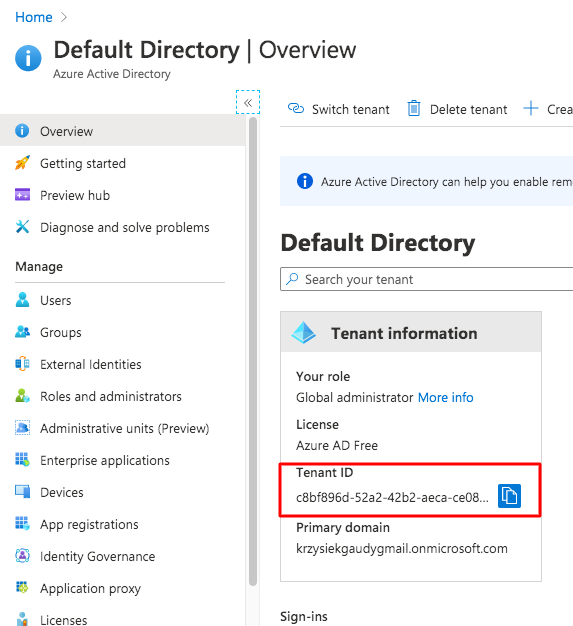
- Select services: Azure Active Directory
- Copy and save Tenant ID (marked on the screenshot)
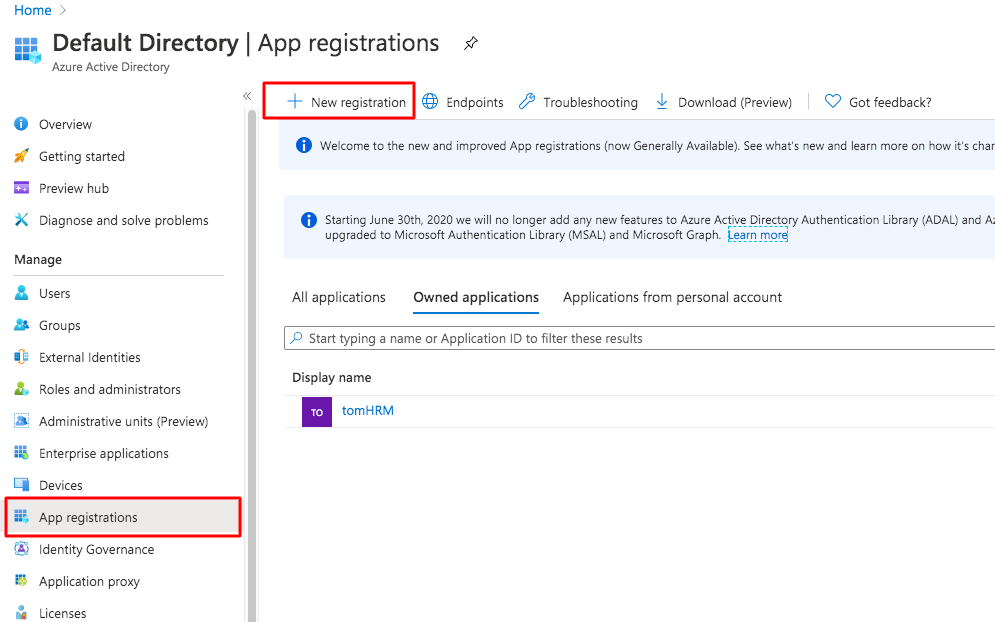
- On the left menu choose App registrations section and New registration
 |
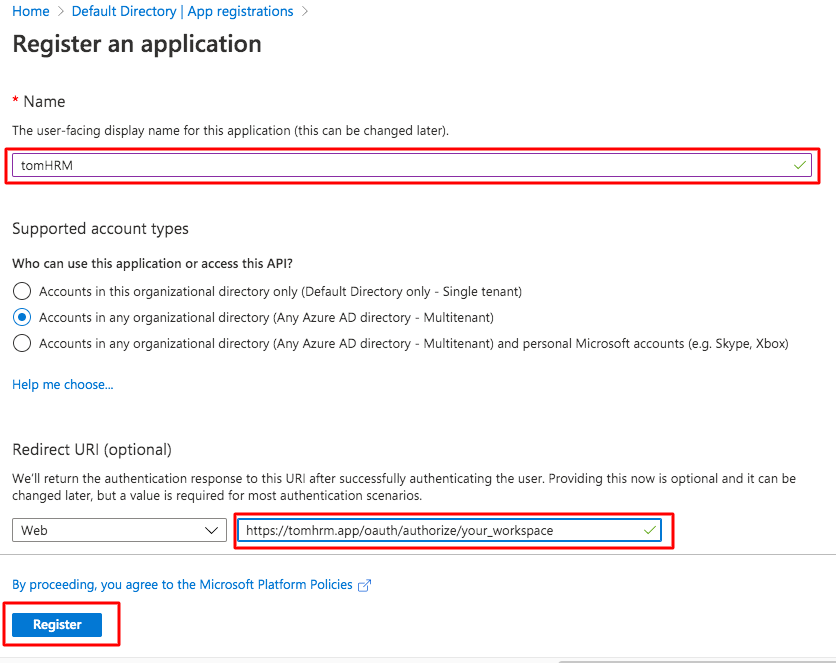
| - Complete the form as shown below. Field Redirect URI fill in the same way as in the screenshot below, but at the end give the name of the organization you have set in tomHRM (workspace)
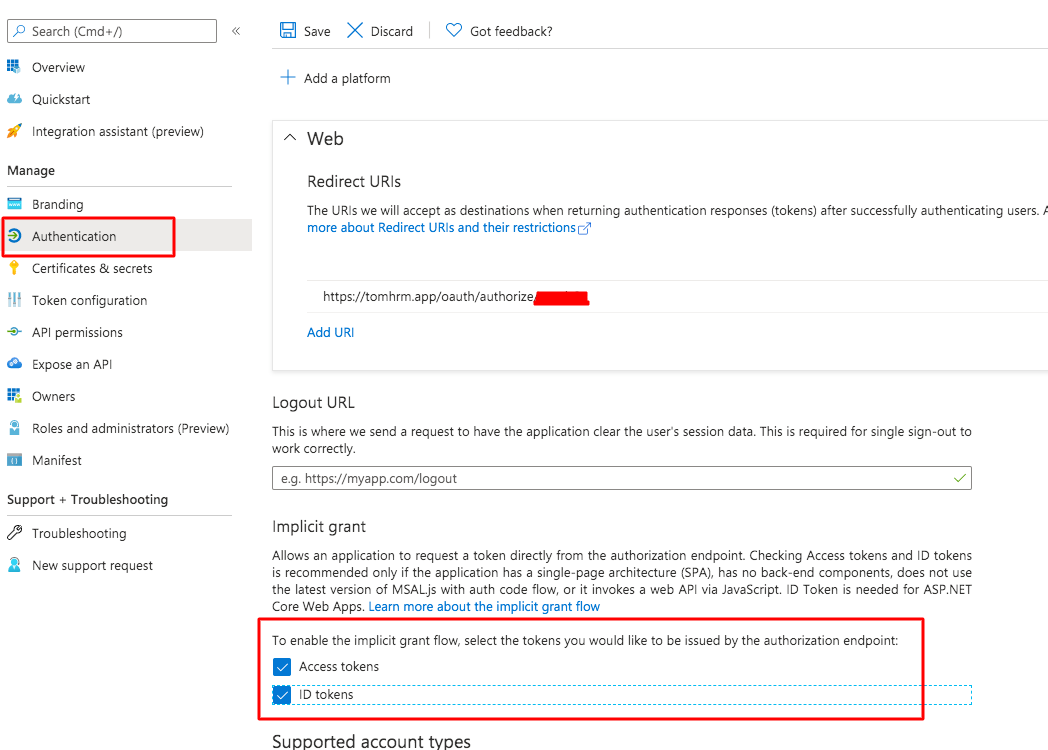
- On the left menu go to Authentication. Select two checkboxes and Save form.
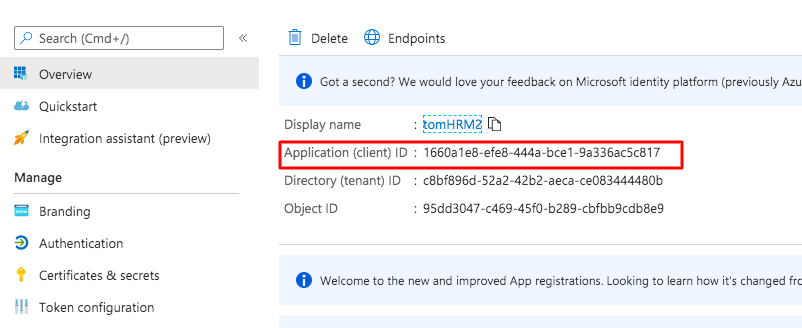
- Go to Overview tab, copy and save value Application (client) ID
Step 2 – Configure tomHRM
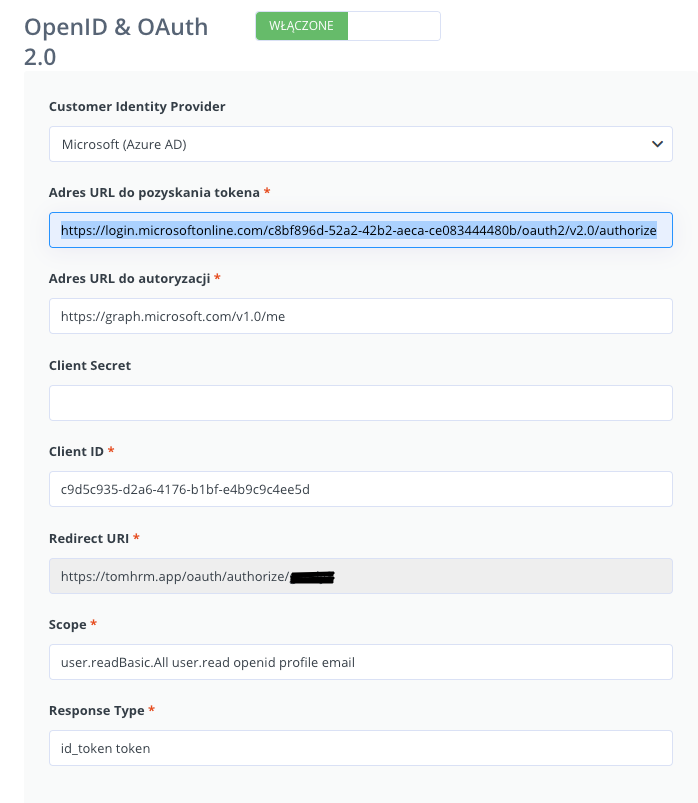
- On the left menu go to Settings > Settings > Authentication and turn on Single Sign-on
- Choose
- User Identity Provider as Microsoft (Azure AD)
- URL token: https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/authorize
,where value {tenant_id} replace it with the value previously copied from your Azure account (Step 1 point 3 above),
e.g.: https://login.microsoftonline.com/c8bf896d-52a2-42b2-aeca-ce083444480b/oauth2/v2.0/authorize - Auth URL: https://graph.microsoft.com/v1.0/me
- Make sure that the Redirect URI that the tomHRM application automatically fills in is the same as the value you entered on the Microsoft Azure configuration pages in Step 1 point #6 above.
- Client Secret – null.
- Client ID: enter the value you wrote down earlier (Step 1, point #7 above).
- Scope: user.readBasic.All user.read openid profile email
- Response Type as: id_token token
- Click Save
Step 3 – Connect Azure AD and tomHRM
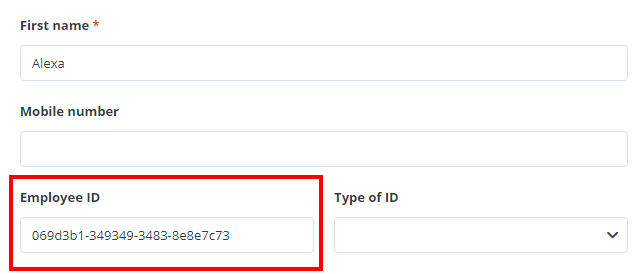
tomHRM authorizes users from Azure AD based on a unique employee ID or email.
If the employees listed in Azure AD have the same emails defined in the tomHRM defined, the setup is complete.
Otherwise, associate employee accounts by providing identifiers.
- In the Azure Portal go to Azure Active Directory and choose on the left menu Users
- Each user on the list is assigned a unique identifier
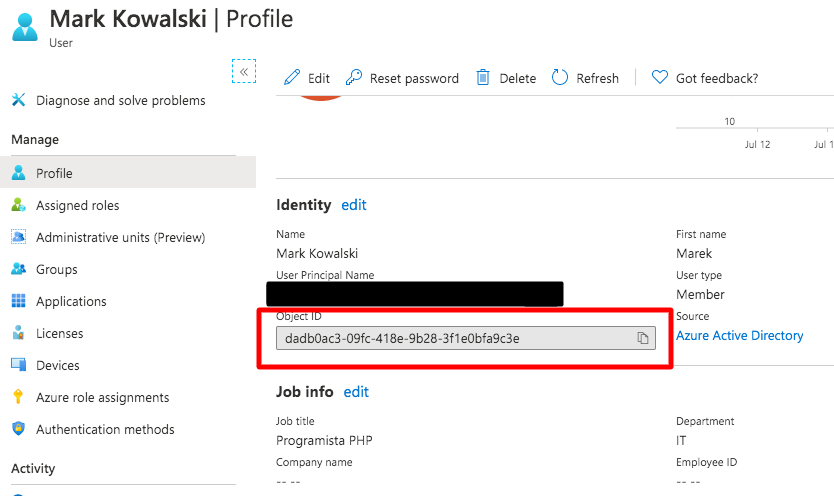
- Employee ID marked in the screen should be entered in the “Identifier” field in the employee profile in the tomHRM